Decoding UMTS (3G) interfaces with Wireshark
Posted May 24th 2010
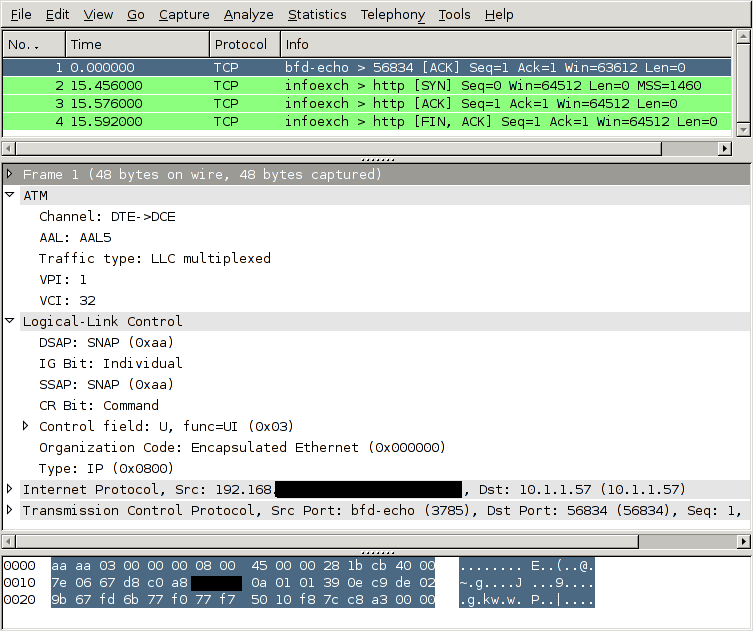
Many 3G networks use ATM on their internal interfaces, e.g. on the Iub and Iu-PS interfaces. Those interfaces carry both control information (radio environment information, attach/detach messages, location updates) and also subscriber data, for instance IP traffic.
Wireshark understands how to decode those ATM interfaces. Here's an example of an interface sniffed by a GTH. The interface was carrying IP traffic over ATM on an E1 line.
How to tell the GTH to capture an ATM link
To look at a 3G network like this, you need to:
- Connect one of the GTH's E1 interfaces to the E1 (or T1) interface carrying the ATM interface. You typically do that at a cross connect panel, using a G.772 monitor point.
- Enable the E1 interface you connected.
- Tell the GTH to start decoding ATM AAL5 (and/or AAL2) on that interface
- Convert the captured data to the file format which wireshark understands, libpcap.
- Open the captured file in wireshark. (It's also possible to pipe the captured data into wireshark live, both on Windows and Unix-like OSs).
Taking those steps one at a time, starting with #2:
Enable the E1 interface
<set name='pcm3A'><attribute name='monitoring' value='true'/></set>
Tell the GTH to start decoding ATM AAL5
IP traffic on ATM is always carried in AAL5. The timeslot arrangement is usually 1--15 + 17--31. A few sites share the E1 with other protocols, this is called fractional ATM. The GTH can handle either scheme.
<new>
<atm_aal5_monitor ip_addr='172.16.2.1' ip_port='1234' vpi='0' vci='5'>
<pcm_source span='3A' timeslot='1'/>
<pcm_source span='3A' timeslot='2'/>
<pcm_source span='3A' timeslot='3'/>
..
<pcm_source span='3A' timeslot='15'/>
<pcm_source span='3A' timeslot='17'/>
..
<pcm_source span='3A' timeslot='31'/>
</fr_monitor>
</new>
In this example, the VPI/VCI is 0/5. If you know the VPI/VCI in advance, great. If you don't, the GTH can sniff traffic at the AAL0 interface and show you which VPI/VCI are active on the link.
Convert the captured data
GTH sends out data in a format described in the API manual. Wireshark wants the data to be in libpcap format. save_to_pcap.erl, in the sample Erlang code for GTH can do the conversion, like this:
save_to_pcap:from_file("/tmp/captured.raw", "/tmp/captured.pcap").
A lazier approach is to let save_to_pcap.erl configure the GTH and start the capture:
save_to_pcap:aal5("172.16.2.7", "3A", lists:seq(1,15) ++ lists:seq(17,31),
{0,5}, "aal5.pcap").
The C version of save_to_pcap can currently only convert MTP-2, not AAL5. If you want it extended, send mail (address at top right).
Start up wireshark
Recent versions of Wireshark, e.g. 1.2.7, can decode such capture files out of the box, without any configuration. Finished.
Permalink | Tags: GTH, telecom-signalling, wireshark